Introduction
Ok these are a really simple UAC bypass from a userland GUI perspective. This is about increasing process integrity levels
it’s not about performing LPE from low integrity to high/SYSTEM with no interaction. These clearly work
in older version of Windows as well but since Windows 11
will be the current version in the near future I thought it was fun to re-visit these!
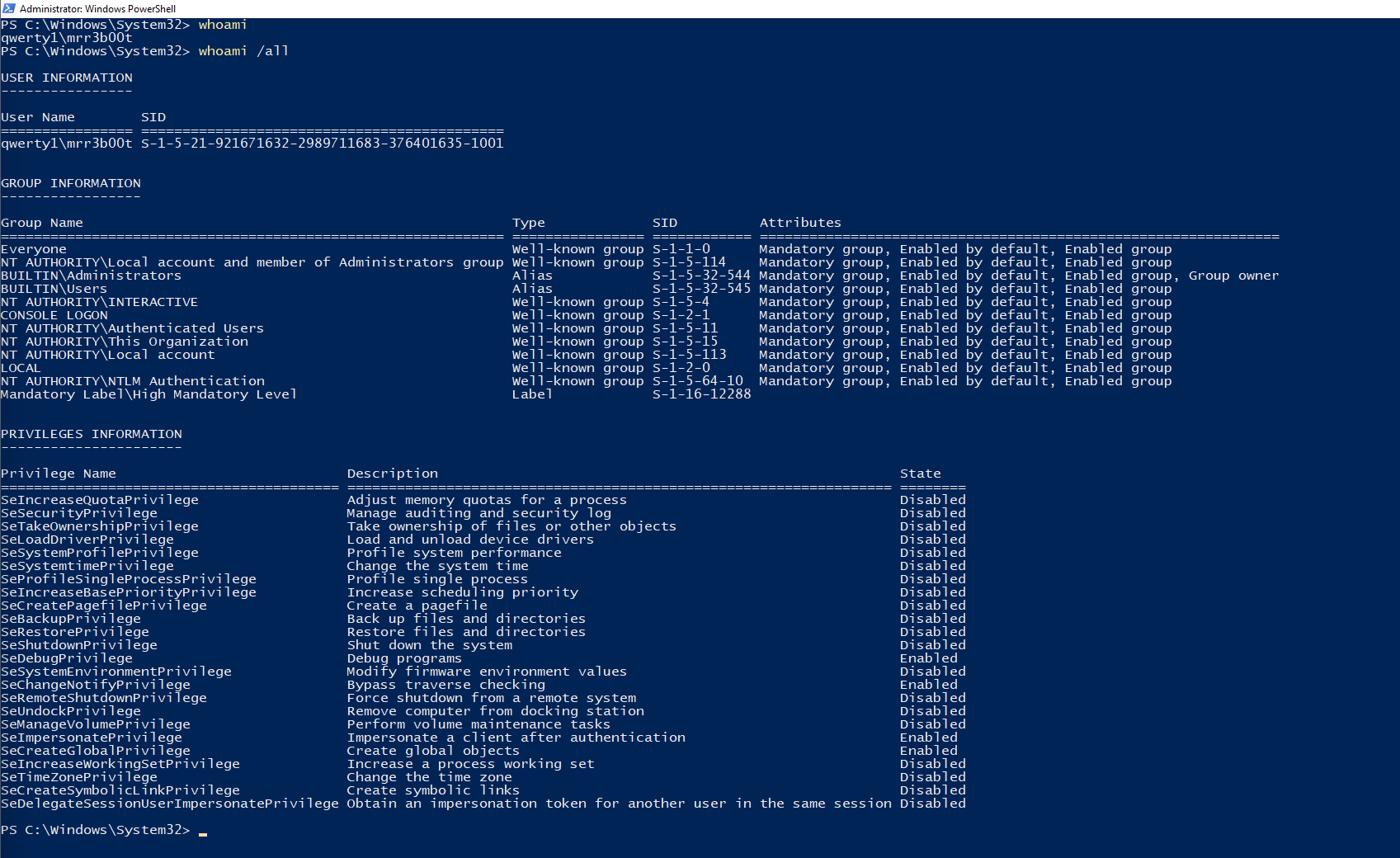
And just to be clear, a medium integrity process as an administrator user will have the following privileges:
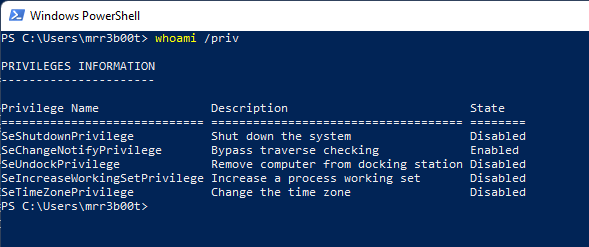
We are going to open another process running on high integrity without knowing the credentials.
Bypassing UAC like a Boss
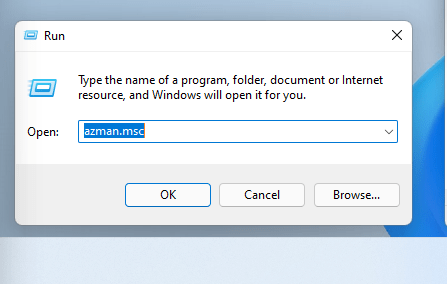
azman.msc
Run azman.msc
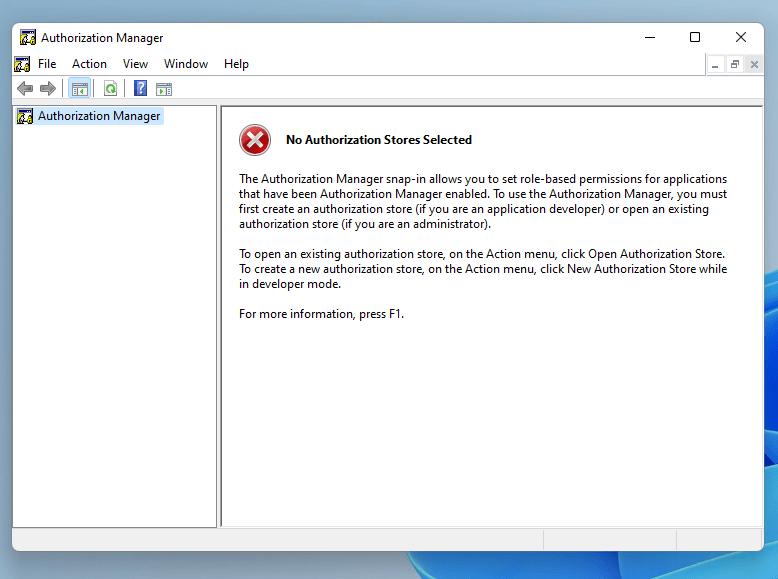
Click Help
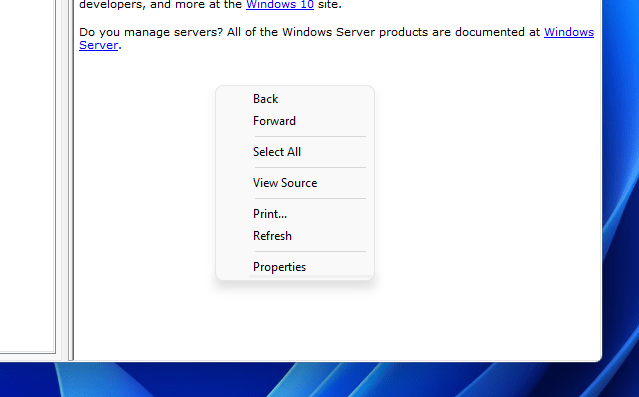
Right click on the right-hand pane and click VIEW SOURCE
From notepad click FILE OPEN
Right click + shift and click open powershell window here
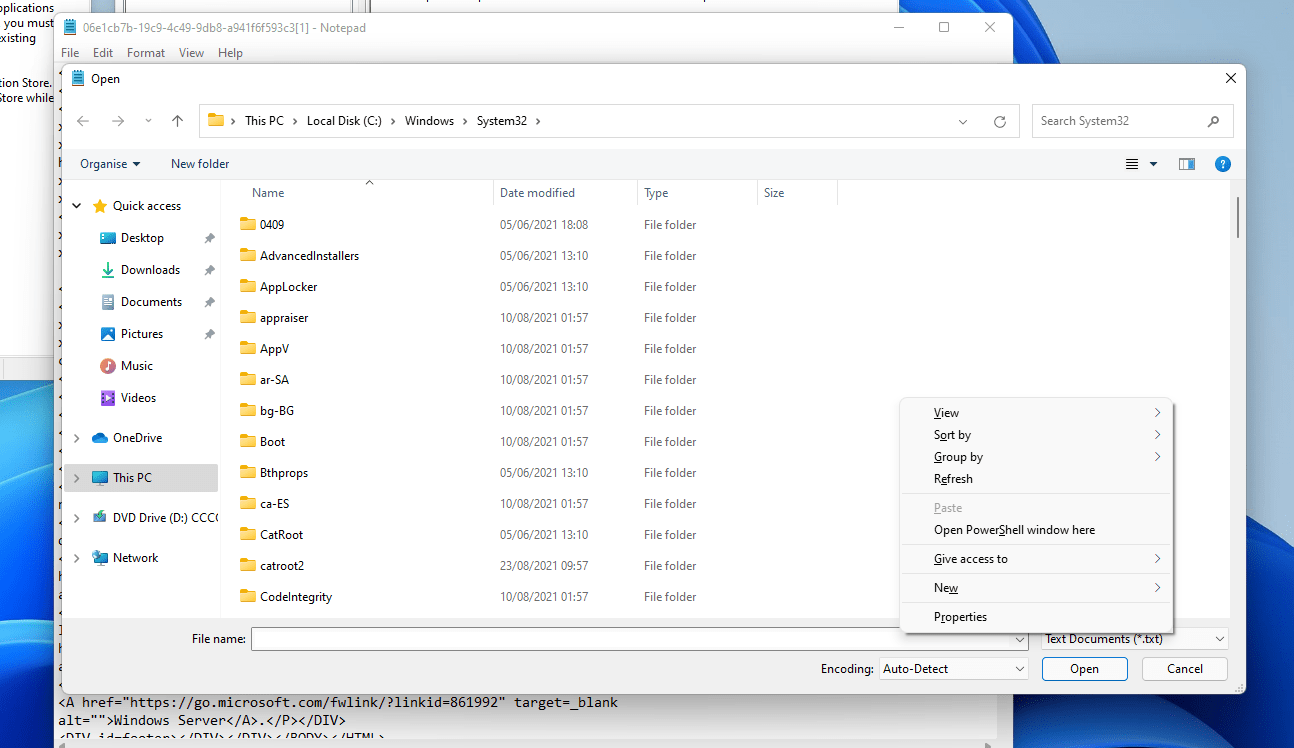
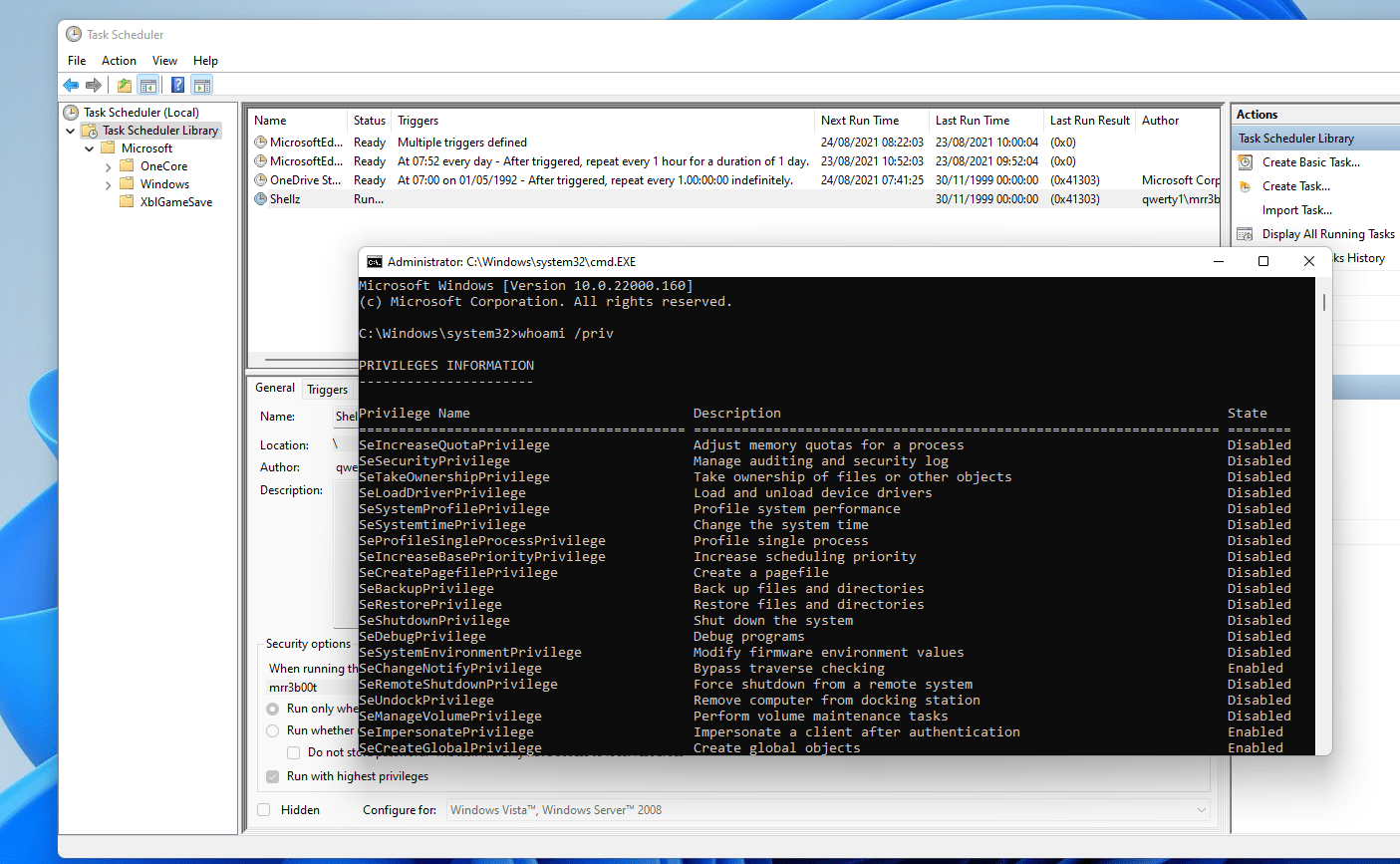
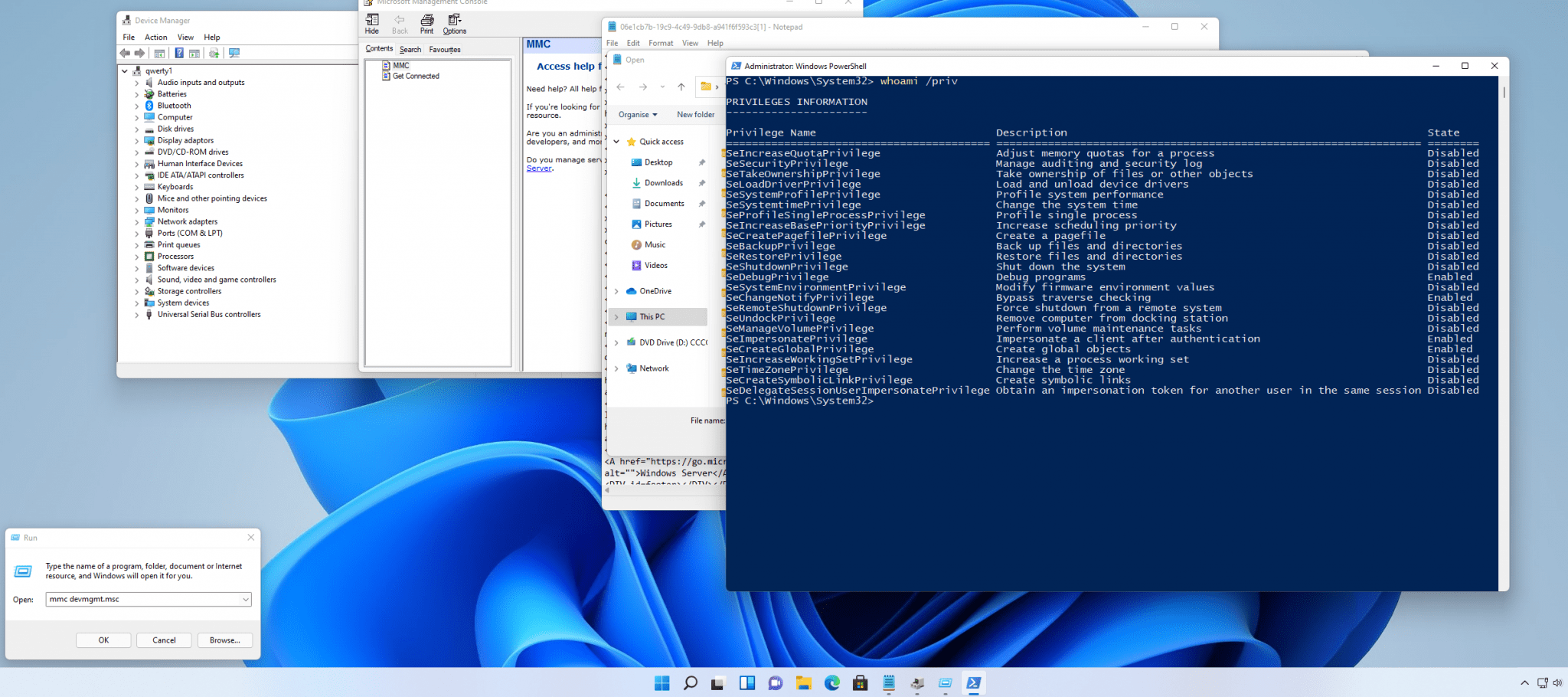
And now you have a process with high integrity
Msconfig UAC Bypass
The use case for this bypass is when you have access to the session but DO NOT have the credentials.
Open msconfig.exe
Click on the 'Tools' tab
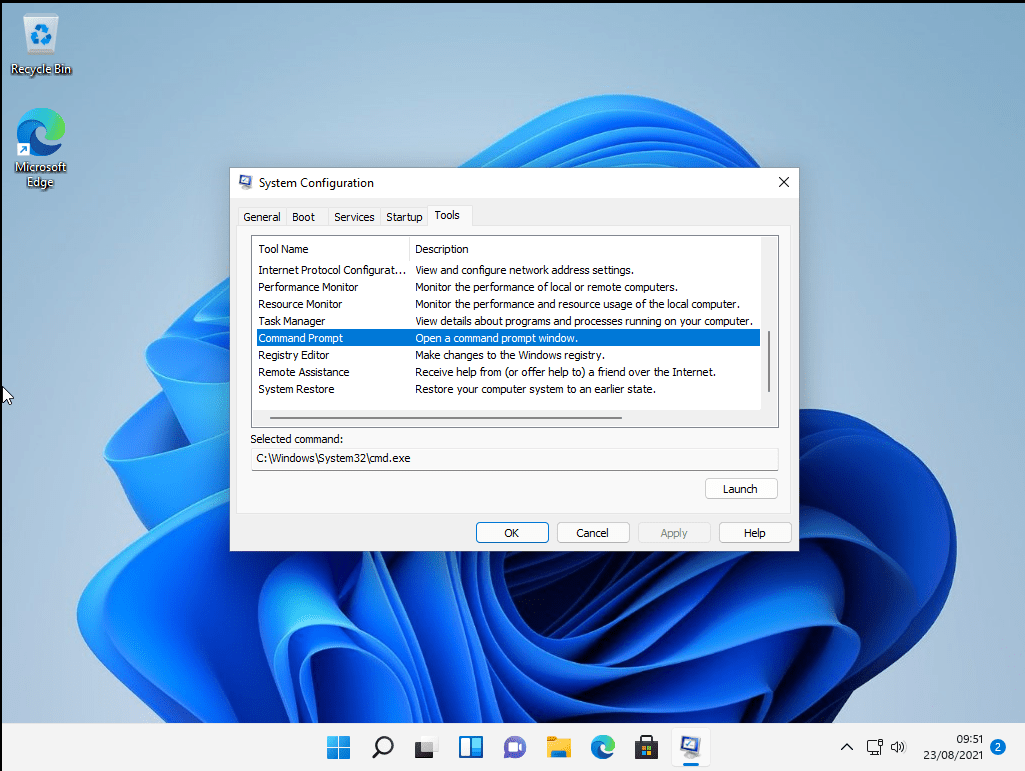
Congratulations, you are now running cmd with the highest privileges.
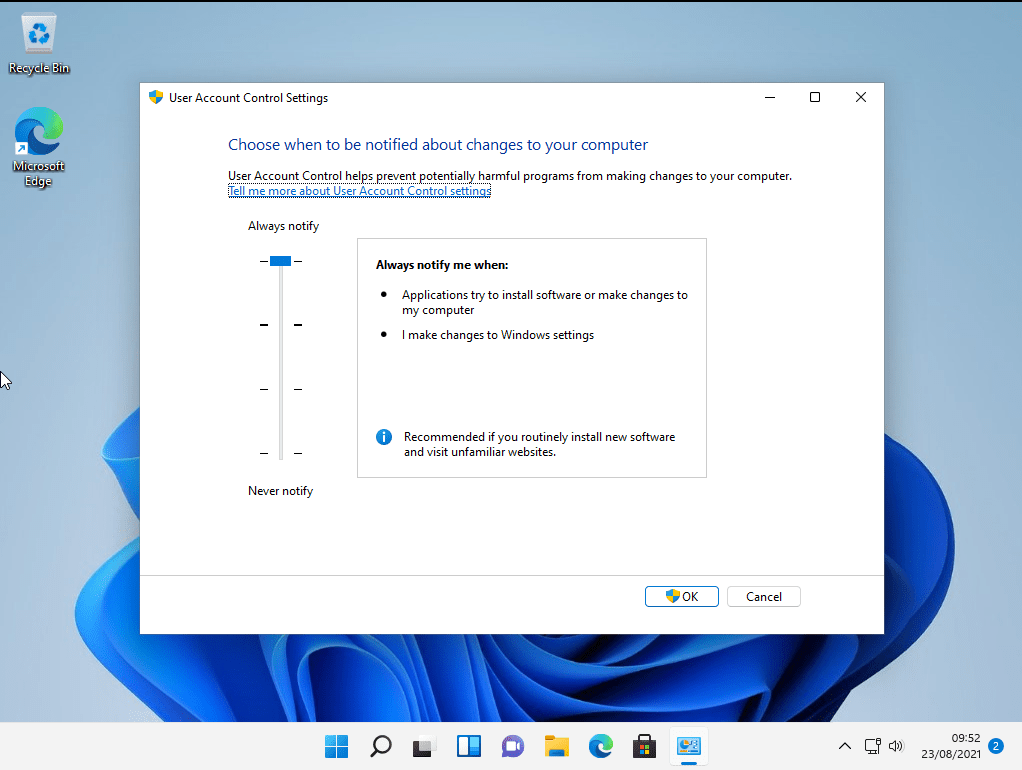
iscsicpl.exe
Another method comes from running c:\windows\system32\iscsicpl.exe

Click No
Click CONFIGURATION
Click REPORT
Right Click + SHIFT and Open Powershell
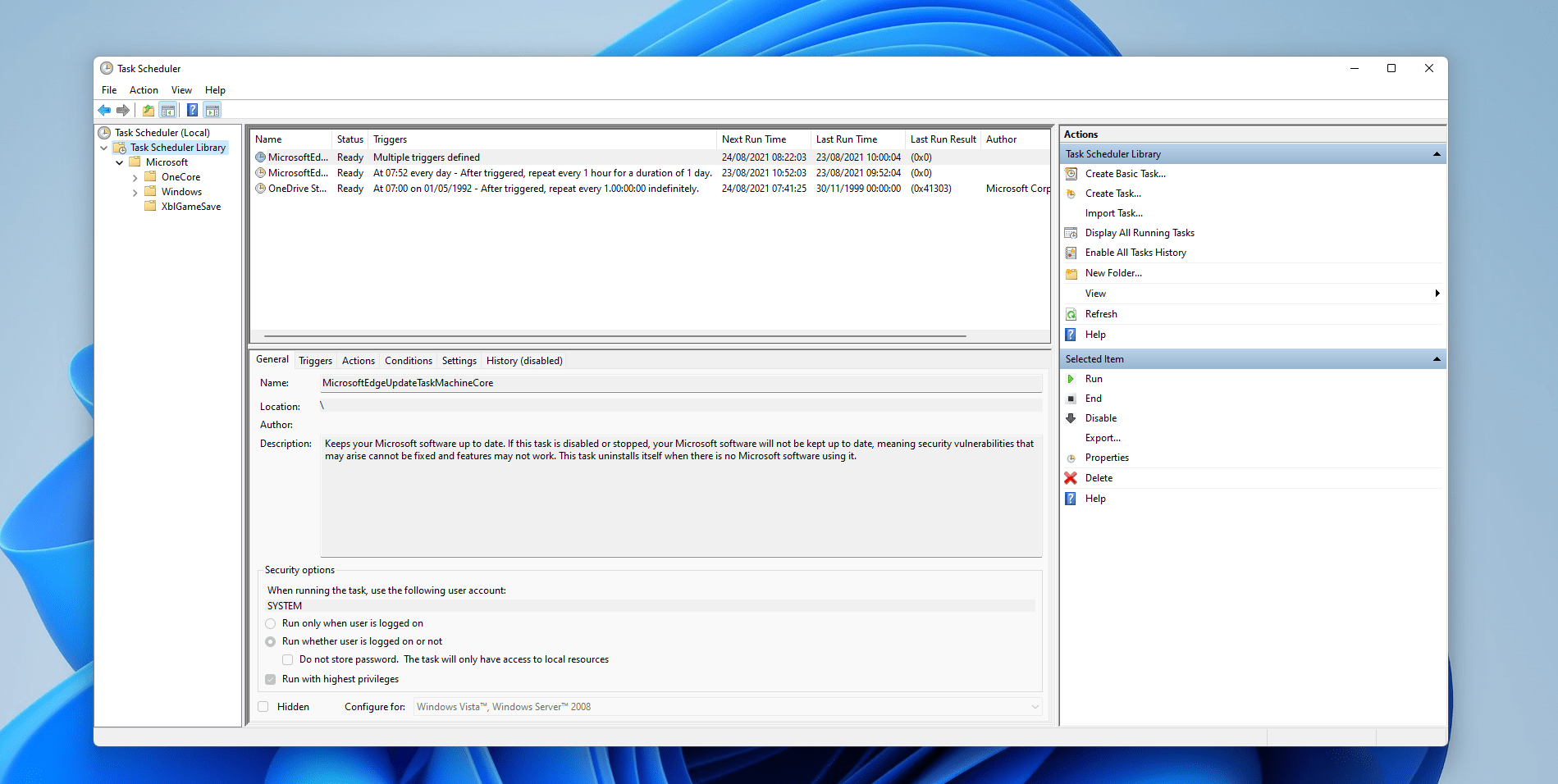
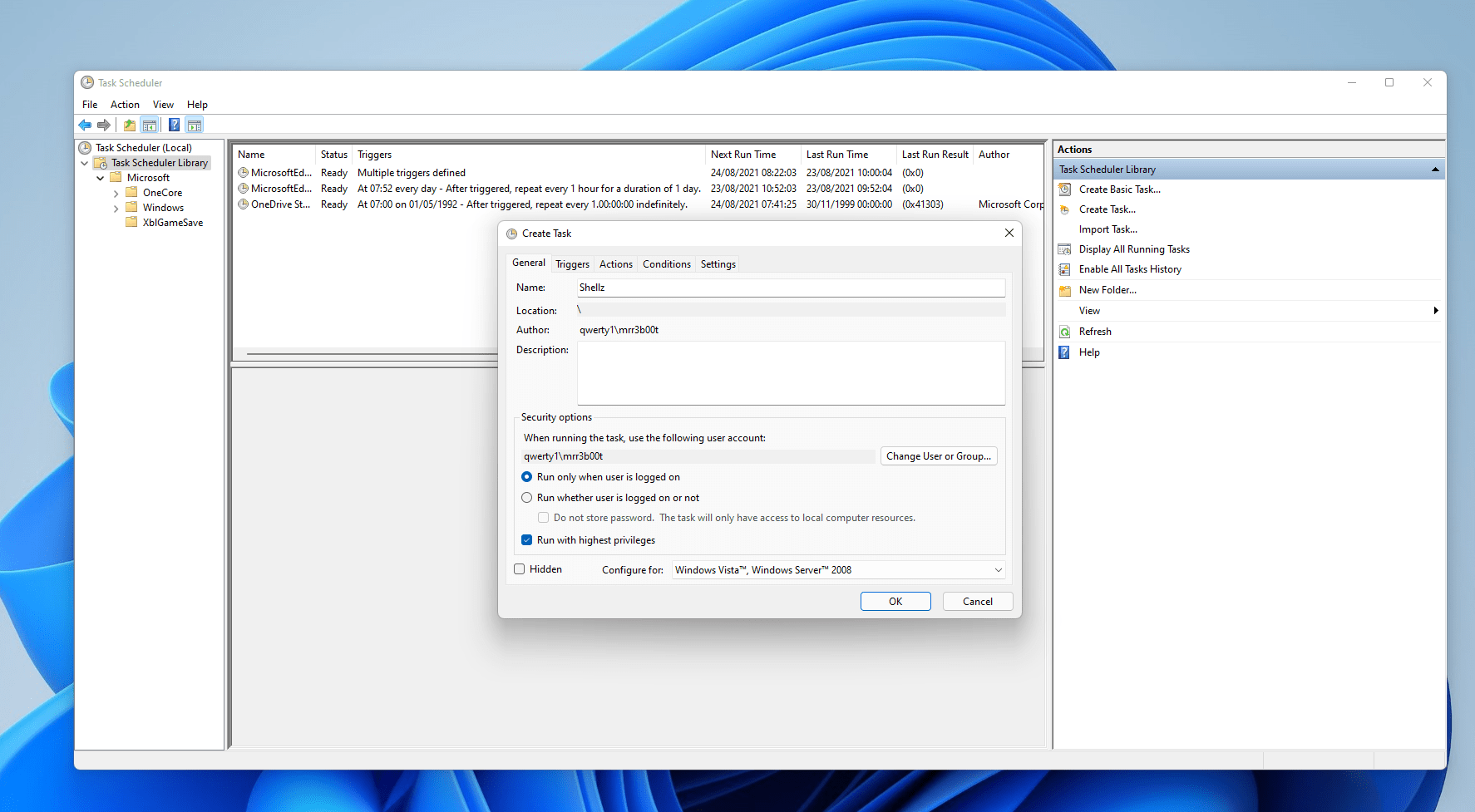
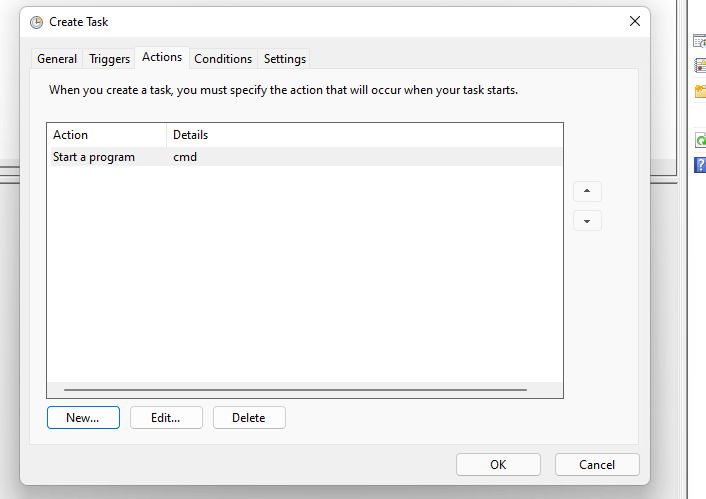
Task Scheduler

MMC/Device Manager/Group Policy Editor etc
Run
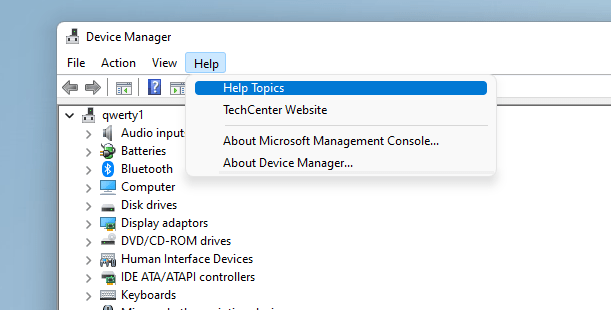
mmc devmgmt.msc
Click Help
Help Topics
Rick click and view source
Use the file open and then RIGHT CLICK + SHIFT to launch a shell
MORE
Ok so we get the gist of how to exploit this manually so what we need is a list of more binaries we can use:
- netplwiz.exe
- dcomcnfg.exe
- perfmon.exe
- compMgmtLauncher.exe
- eventvwr.exe
So theres lots of ways of doing this via binaries.
Summary
These might seem like they are not useful, but you can find position where these can be exploited. It’s often the small things that make a difference.
.png)